How to Stop Windows 10 Updates
First the bad news, Win10 mandates mandatory updates. There is no button to turn off updates. The enterprise edition allows updates to be delayed and rolled out in batch, but there is still no button to turn it off.
The good news is, there are (at least) two ways to stop automatic updates: 1. disable the service, or 2. block the update program in the Windows firewall. Exact instructions for implementing both methods are given below. The first method is easier, but less granular. Less granular means that it will apply to all users and all user groups. The second method is more complicated to implement, but more granular. More granular means that automatic updates can be configured to run only for certain users or user groups and not to run for others (i.e., policy defined). This would allow you to log on as user Nyet-update most of the time and not be bothered with updates running in the background and locking up CPU and bandwidth, and then later, when you have plenty of time and bandwidth, you could log on as user admin and let the updates run their course. Of course, you can permanently stop updates, too, using either method. Either method will work alone; you don't need both of them. Method 1. disable the service (permanently applies to all users) Step one. Press the Windows key and s. This opens the search function. In the search entry field type "services" (without quotes). Click on "services desktop app" in the search list. This opens the MS services java thingy. 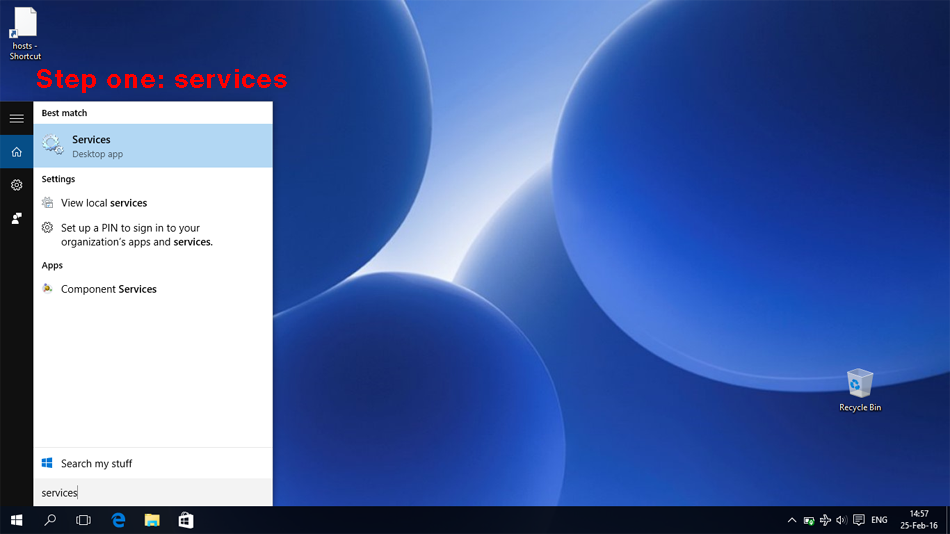
Step two. In the services java thingy, scroll down to the bottom and locate the service titled "Windows Update". 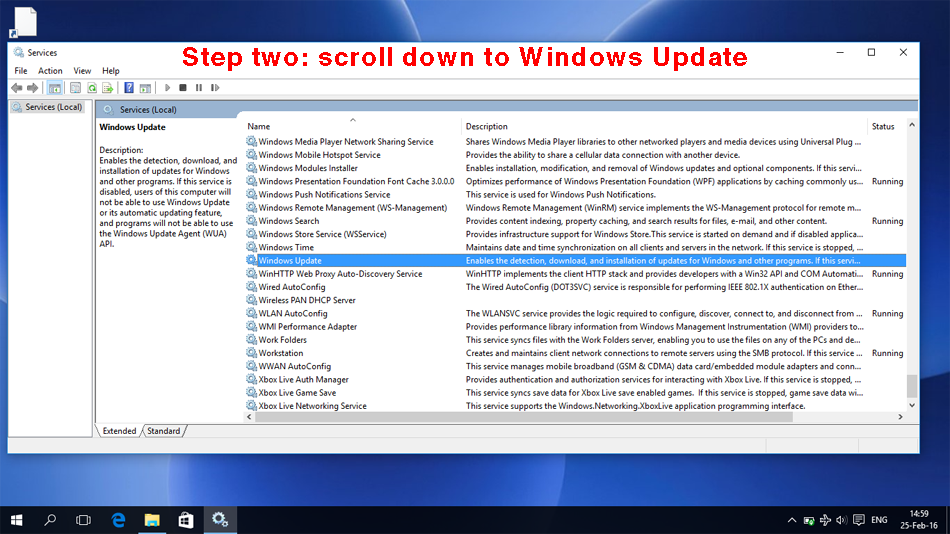
Step three. Right-click on this and, in the context menu, activate the function "properties". This opens the properties java thingy for that service. 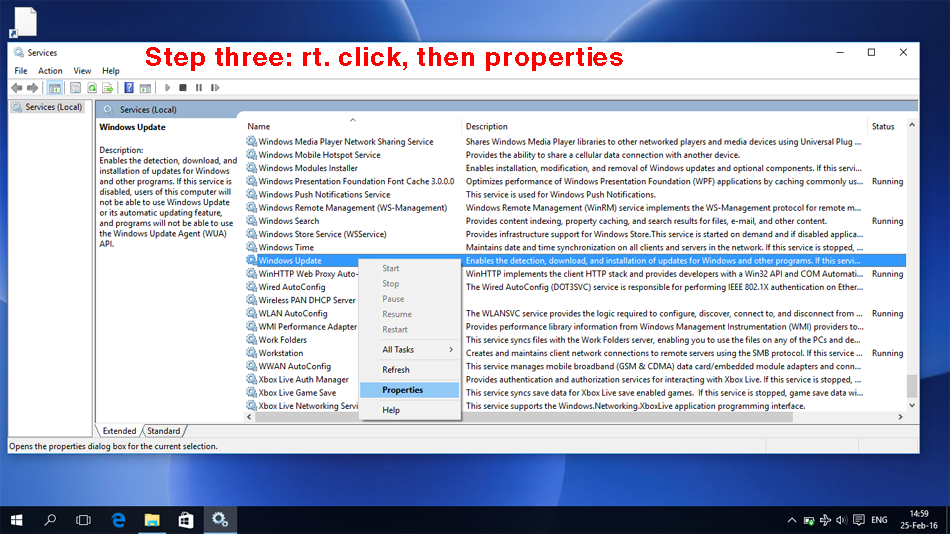
Step four. In the properties java thingy, change the startup type to "disabled", and under service status click "stop". Then click "apply" and "ok". That's all there is to it. This setting survives a cold restart. 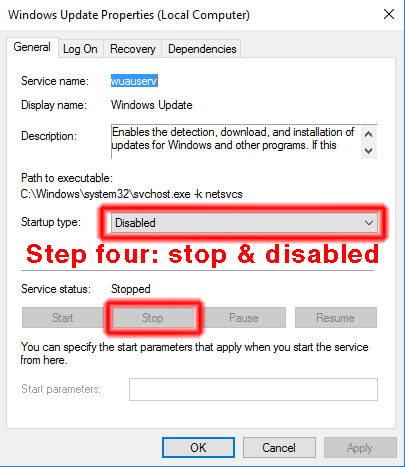
Method 2. block the update program in the Windows built-in firewall (policy defined) Step one. Press the Windows key and s. This opens the search function. In the search entry field, type "firewall" (without quotes). Click on "Windows firewall" in the search list. This opens the Windows firewall java thingy. 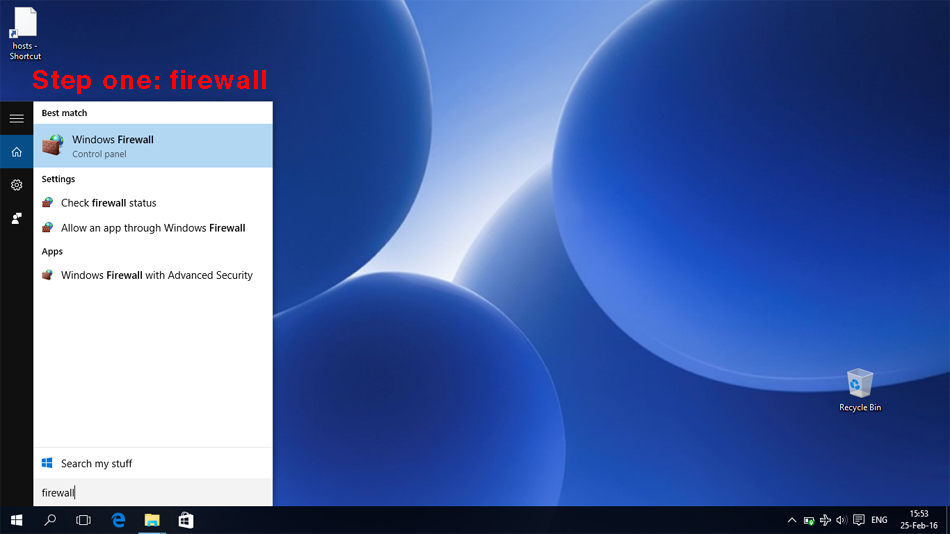
Step two. In the Windows firewall java thingy, click on "advanced settings". This opens another java thingy titled "Windows Firewall with Advanced Security." 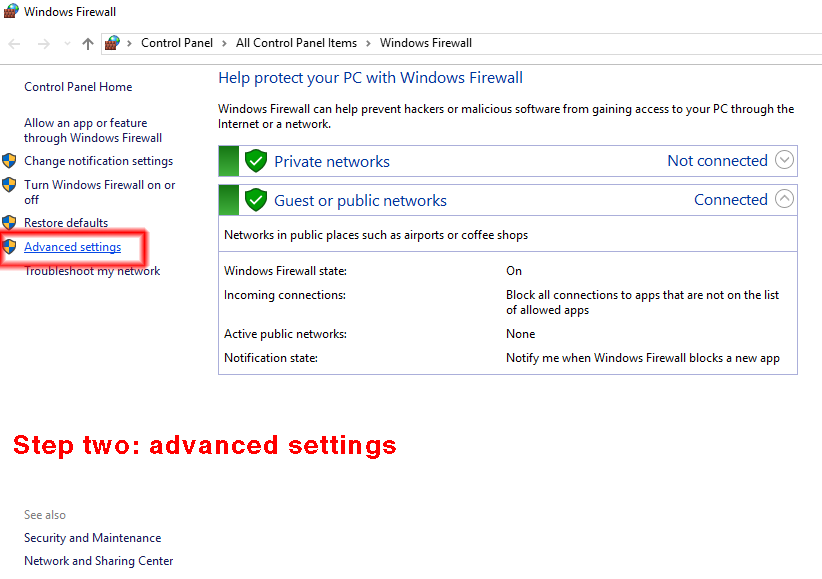
Step three. In the left-most panel of the java thingy titled "Windows Firewall with Advanced Security" click the function "outbound rules". This will bring up a list of pre-configured rules. 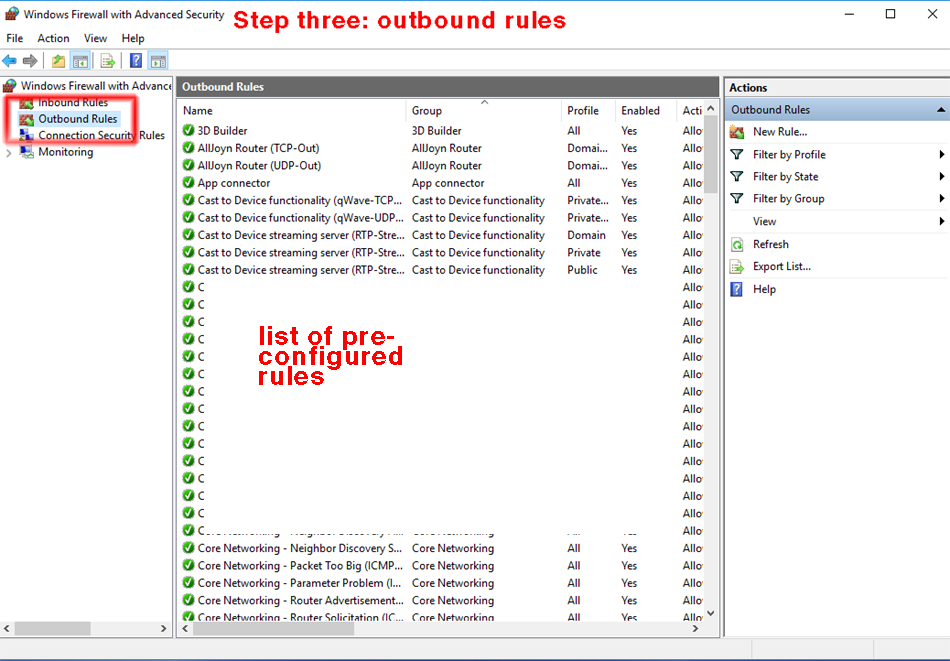
Step four. In the right-most panel, click the function "new rule". This brings up another java thingy titled "new outbound rule wizard." 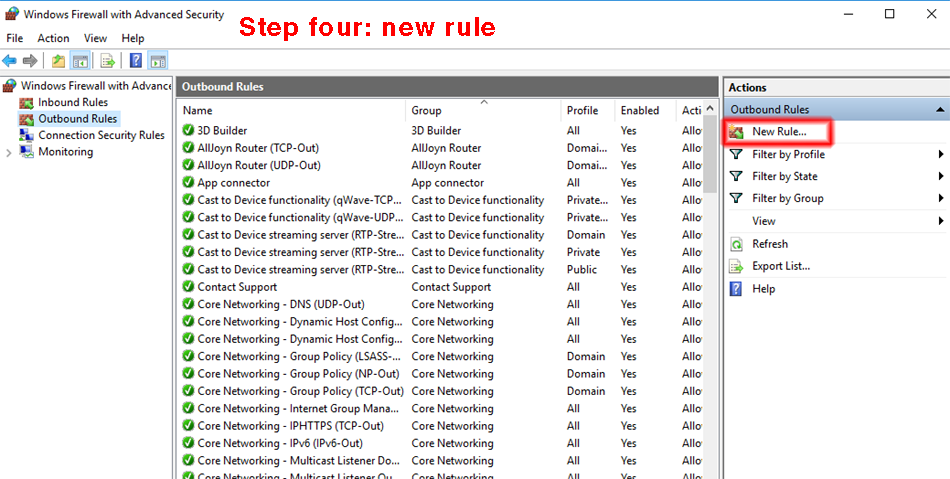
Step five. In "rule type" page of the new outbound rule wizard, click the radio button "program", then "next". This brings up the next page in the new rule wizard. 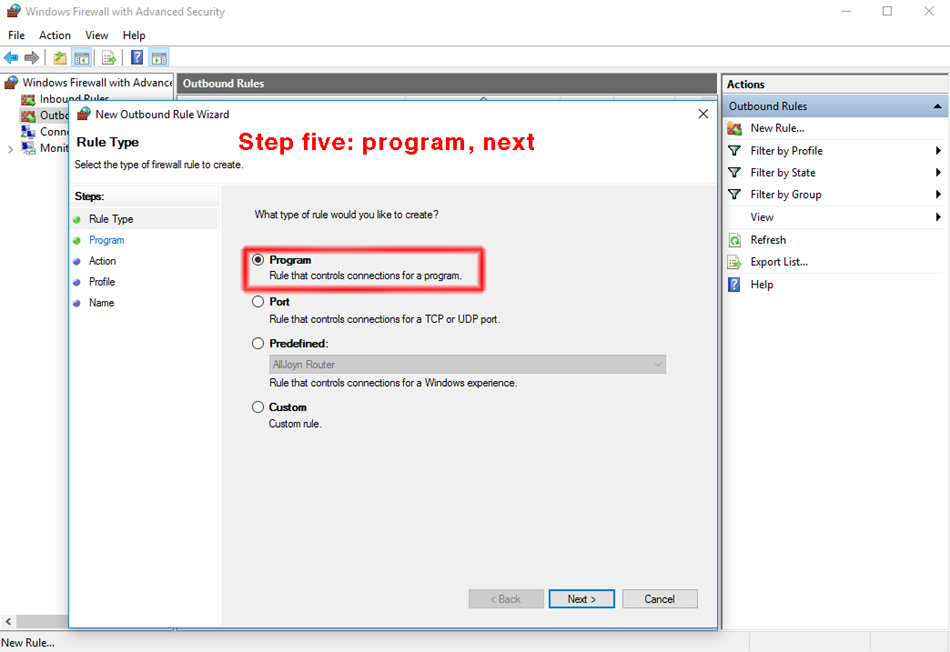
Step six. In the "program" page of the wizard, click the radio button "this program path" but not yet "next". Step seven. This is the only tricky part, in that you might have to navigate the Windows file structure to find the following .exe file: WindowsUpdateElevatedInstaller.exe If Win10 was installed in the default location, then just copy-paste the complete file name and path from the line in these instructions immediately below into the entry field to the left of the "browse" button and then click "next", as illustrated below. The complete file name and default path (copy-paste if Win10 is in the default location): %SystemRoot%\System32\WindowsUpdateElevatedInstaller.exe 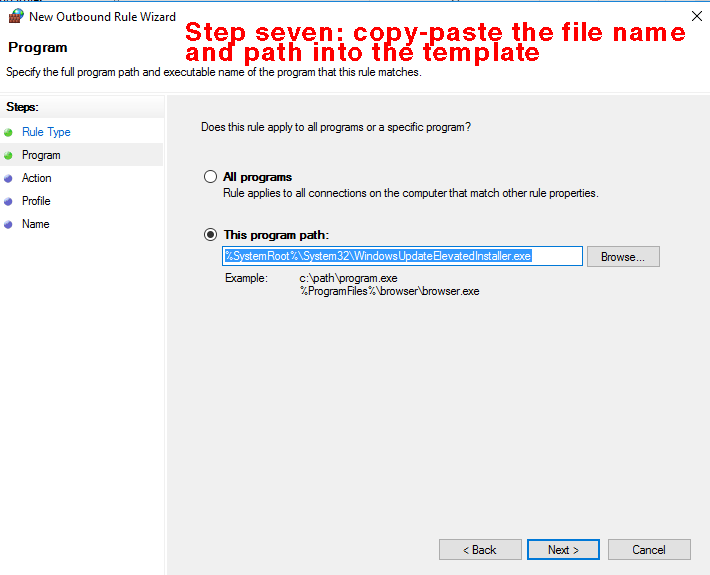
If the file is not located in this path, then you will have to locate the file yourself (in some other directory or on some other partition) by clicking the "browse" button and navigating as illustrated below until you find the file WindowsUpdateElevatedInstaller.exe; then click "open" (DUH--of course you don't really open it, you just link it to the firewall rule). 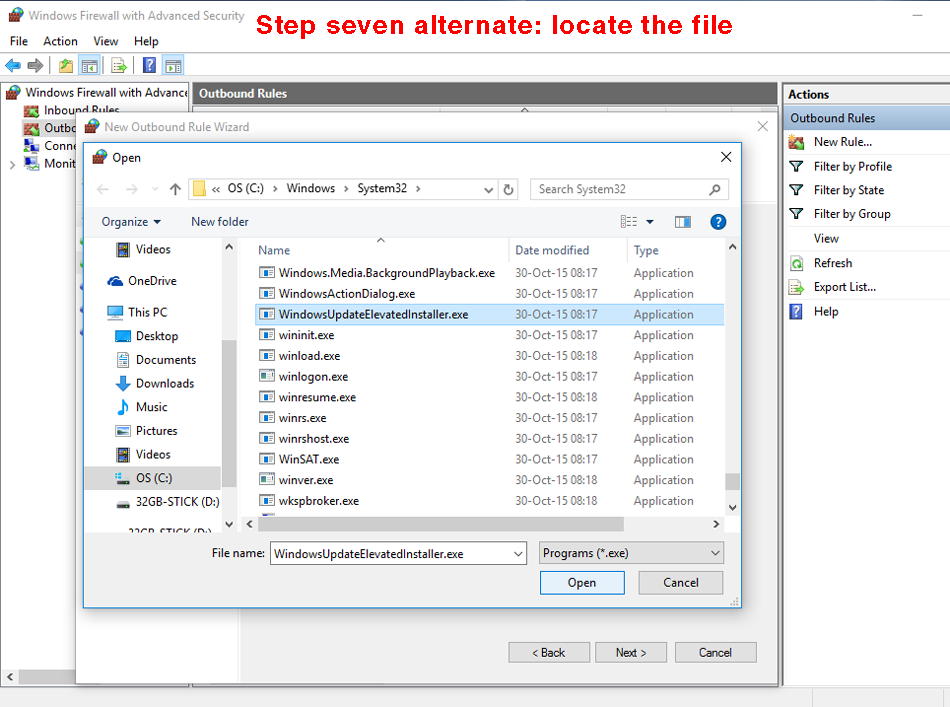
Once you have the file name and full path in the entry field in the "program" thingy above, click "next". Step eight. In the next panel, titled "Action", of the new outbound rule wizard, activate the radio button "Block the connection" and then "next". 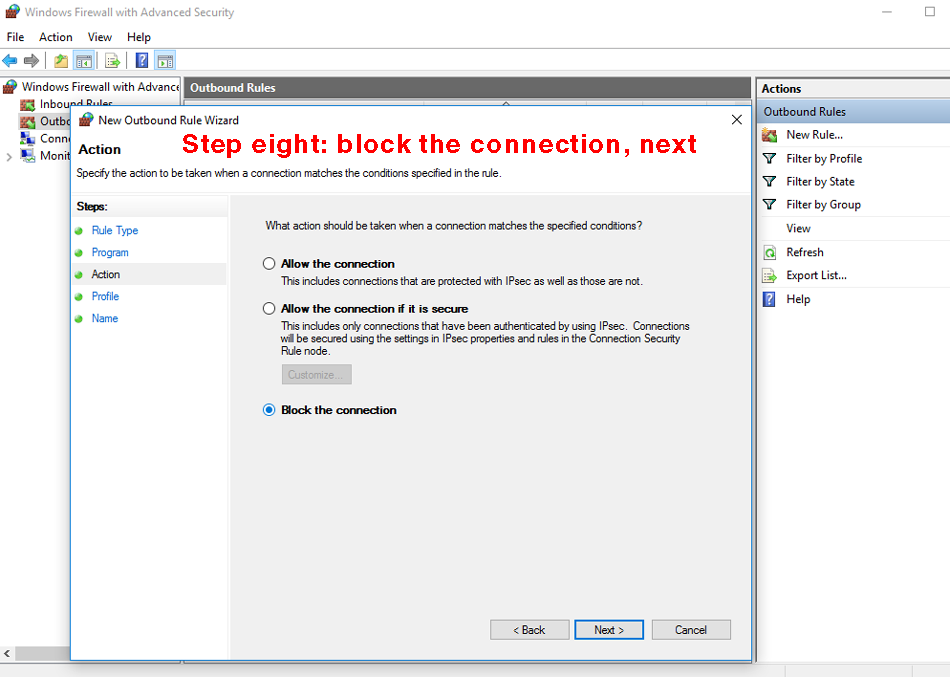
Step nine. I know, this is getting tedious. The next page is for enterprise sys admins and allows granular control of the firewall rule. The next panel [see below], titled "Profile", allows you to specify the network environments in which the rule should apply: a trusted network (e.g., corporate domain or private-home network) or an untrusted network (e.g., public WiFi hotspot). If you know what you're doing, activate the appropriate ones; if you're not sure, activate them all; then click "next". 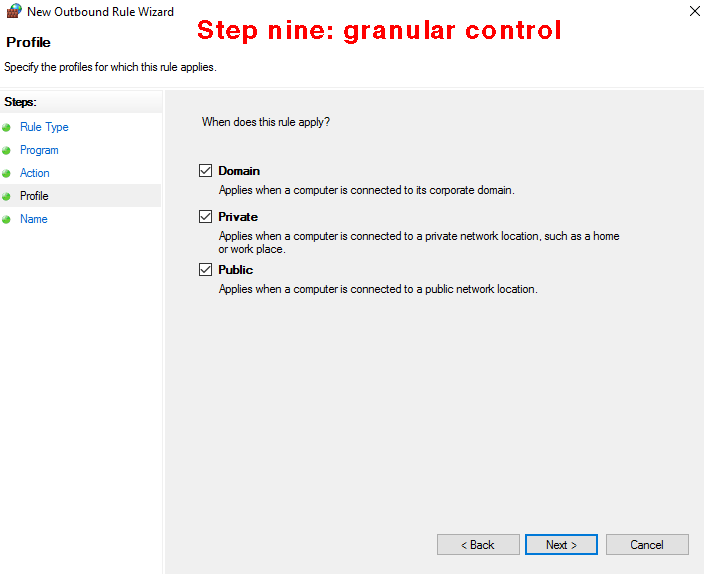
Step ten [last]. The next page allows you to give your rule a name to remember it by (e.g., "block updates"). Then click "finish", and you're done. 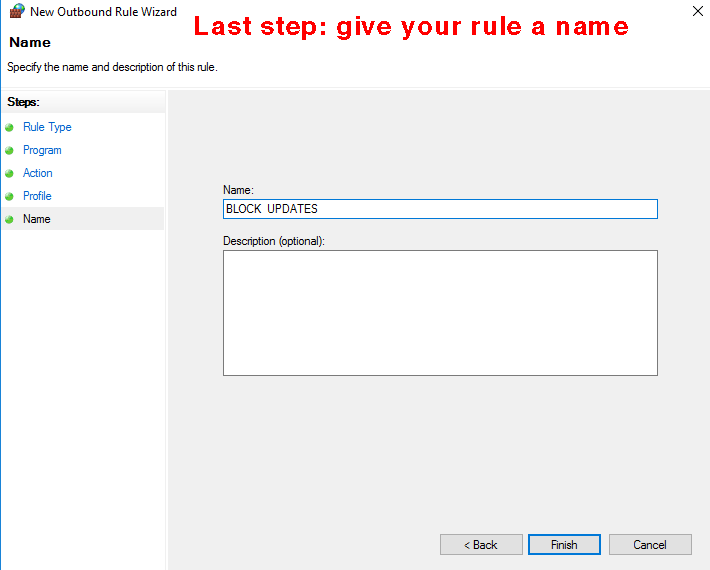
Upon successful completion of the above steps, you should be returned to the advanced security page of the firewall config wizard [see below]. You should see your new rule at the top of the list (in this example, I also blocked McAffee). The icon in the left column shows a red circle with a diagonal line through it (a European traffic sign meaning Verboten!) indicating that the rule blocks something. 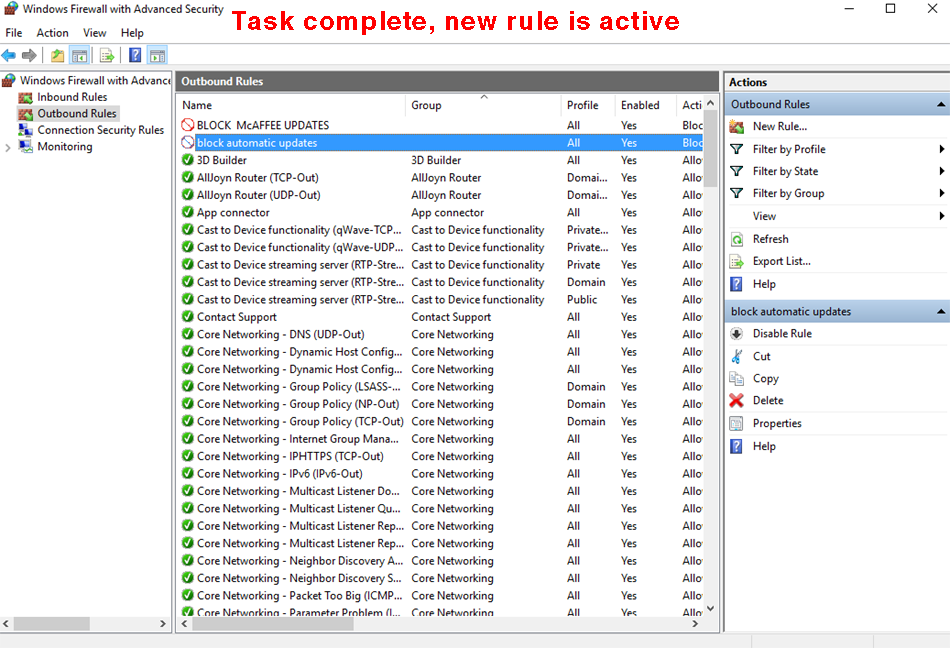
Optional additional config parameters, for professional sys admins and people who know what they're doing: right-clicking the rule opens a context menu, from which you can configure even more granular control (such as binding the new rule to specific users, user groups, IP addresses, and so on). 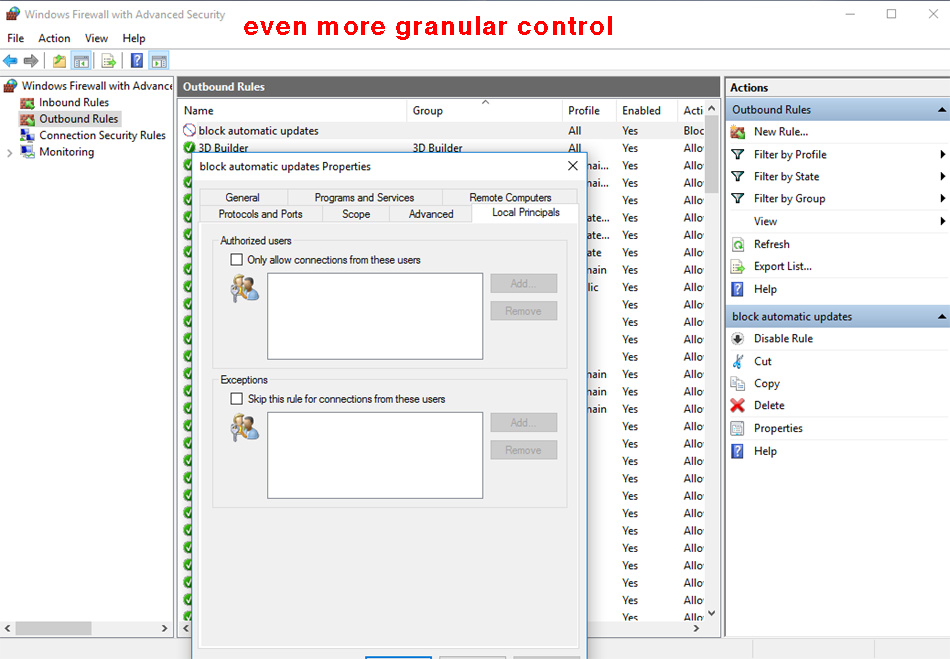
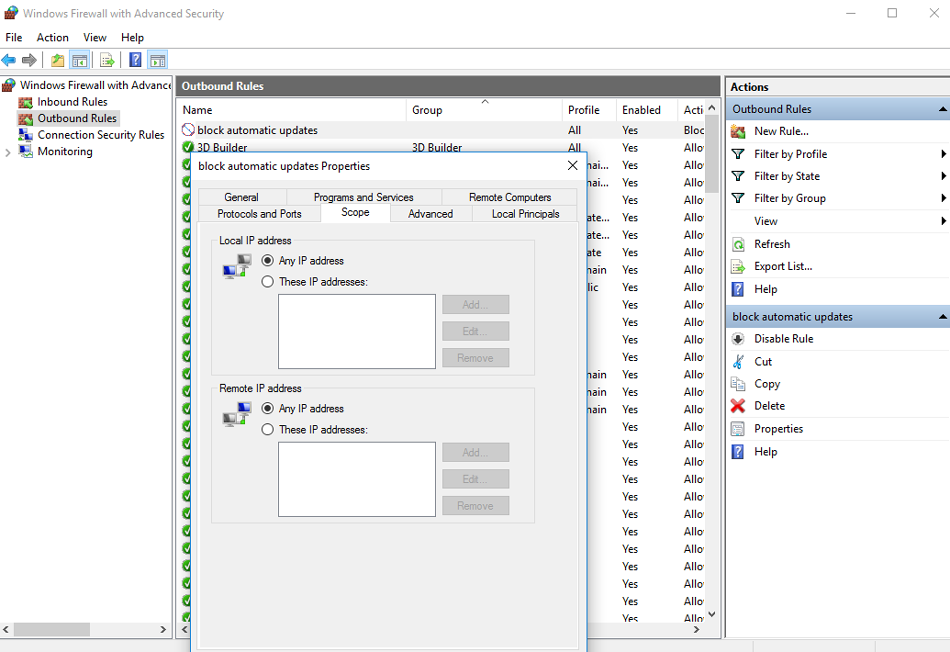
|
|
Windows Defender
The Windows Defender (MS's anti-virus program) can be turned off, but it turns itself back on again after a few minutes. For those who may wish to prevent Windows Defender from locking up CPU and network resources at inopportune moments, the same two methods should work for disabling automatic updates to Windows Defender (and any other network services which are either clogging the network or are otherwise undesired). Either 1. disable the function in the services java thingy (e.g., Windows Defender Service"), or 2. create a new rule in the firewall to block outgoing connections. For Windows Defender, the default file name and path are: C:\Program Files\Windows Defender\MsMpEng.exe Alternatively, follow the instructions on the page linked below: Click here to learn how to turn off Windows Defender. A few further notes on updates. 1. Win10 lists each installed update. They can be rolled back individually. Just right-click on any one and then click "uninstall" in the pop-up thingy. 2. If you uninstall too many, you can re-install them by reversing the above procedure(s): that is, by enabling the service or by temporarily disabling the firewall rule. However, as soon as Win10 establishes contact with the mother ship, it will download and install all available updates; you cannot choose which ones you want. 3. If, after having re-installed all of them, you still want to uninstall some of them, be careful what you click so you don't have to re-re-install all of them again. 4. Be advised that any Win10 machine which has updated itself will by default feed its updates (both OS and apps!--see below) to any other Win10 machines it can reach which have not yet updated themselves. It may therefore be advisable to block both inbound and outbound connections, if one uses Method 2. (firewall) above. 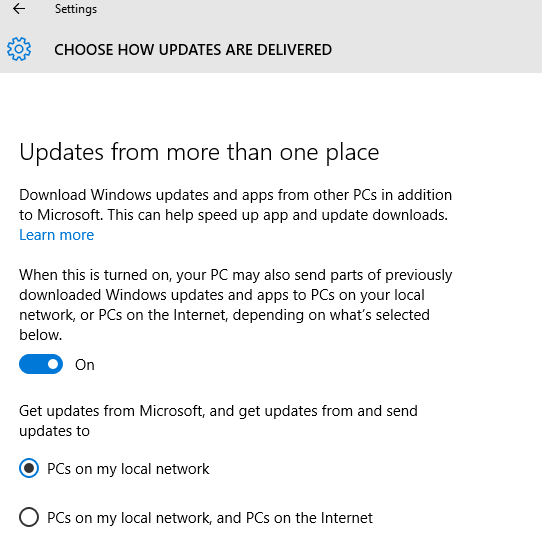
Speaking as a professional networker (certified Cisco and Wireshark), my observation is that Win10 the noisiest OS I have ever seen. Not only the automatic updater and Defender, but many other functions, features, programs, and apps (such as "live tiles", those animated start screen icons which poll the Internet every 15 minutes for current weather, airline flights, stock exchange information, local restaurants and cinemas, geo-location services, etc. etc., "OneDrive", which is the MS version of iCloud, etc. etc.), are going online frequently and chatting up the network. Win10 assumes you want to connect to MS, to send/receive personal account information, error messages and diagnostics, OneDrive (cloud), McAffee anti-virus definitions, network time sync, your personal Internet browsing habits (anonymous profiling in preparation for sending you advertizing--to make your Internet experience ever so much more personal!), and so on and so on. In my opinion, this iteration of Windows may not scale well in enterprise/industrial environments without considerable tweaking and fine-tuning of client stations, as well as some well-thought-out access lists on LAN routers, to dampen down the network chatter, especially over expensive WAN links. Expect the network load to worsen in WLAN environments, due to a) half-duplex operation of wireless, and b) additional overhead of encryption headers. Over a period of about 20 minutes, with Wireshark running, and activating no apps whatever, I identified a number of MS servers to which Win10 had established connections. For the benefit of sys admins who may wish to block some or all of these (with ACLs or whatever), I append a list of DNS-requested names and their resovled IP addresses. Win10 'phone home' servers: ctldl.windowsupdate.com ctldl.windowsupdate.nsatc.net ctldl.windowsupdate.com.edgesuite.net a1621.g.akamai.net 193.247.90.0 /24 (RIPE, Zurich--this will be different for USA and other regions) 193.247.167.0 /24 (RIPE, Zurich--this will be different for USA and other regions) officeclient.microsoft.com prod.configsvc.live.com.akadns.net weu-config.officeapps.live.com osiprod-weu-snow-000.cloudapp.net 23.96.0.0 /13 telecommand.telemetry.microsoft.com telecommand.telemetry.microsoft.com.nsatc.net 65.52.0.0 /14 sls.update.microsoft.com sls.update.microsoft.com.nsatc.net NetRange: 157.54.0.0 - 157.60.255.255 CIDR: 157.54.0.0/15, 157.56.0.0/14, 157.60.0.0/16 65.52.0.0 /14 settings.data.microsoft.com settings.data.glbdns2.microsoft.com onesettings-db5.metron.live.com.nsatc.net 192.232.139.0/24 I cannot guarantee that the above list is exhaustive. I hope this page has been of some use. Flash email: |